If you’re looking for good logging software for your Cisco network or If you’re looking for Cisco security options, then you should download cisco anyconnect immediately. Cisco IOS software offers flexible logging options to achieve visibility goals while also offering basic logging best practices that reduce the impact on your Cisco devices. Check out our free trial offer! Let’s explore the five most crucial logging software for Cisco IOS devices.
Page Contents
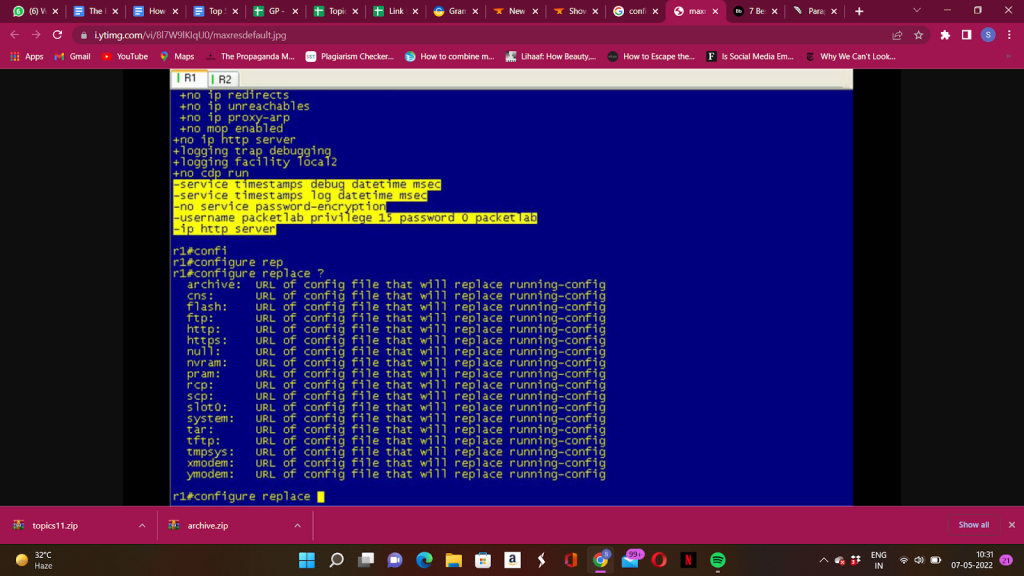
Configuration Replace
The Cisco Configuration Replace software gives permits to restore an IOS router’s earlier configuration state. This operating system substitutes a previously saved configuration file for the current running configuration. This feature is helpful once restoring a device to a previous configuration state and rolling back changes. Configuration Rollback can also be used to reverse the prevailing configuration condition. The instructions that obey characterize the Cisco Configuration Replace software and its operational processes.
To undo ended in failure confirmation adjustments, use the revert instruction. To return to a previous state after exiting configuration mode, a confirmation command is required. When troubleshooting the Configuration Replace characteristic, the revert command to is beneficial. If a problem persists after the transformation, it can return a Cisco router to its initial configuration state. Reverting to a previous configuration state, on the other hand, maybe challenging.
A sealable feature is available to the configuration replace method. When you’re using the configure replace command, the running configuration file is immediately locked for the period of the process. This locking mechanism prevents other users from changing the running configuration while the replacement procedure is running, resulting in the suitable alternative operation having failed. By using the configure replace command with the no lock keyword, you can deactivate the synchronization of the running configuration.
The running configuration lock is automatically cleared at the end of the configuration replace operation. The show configuration lock command displays any existing locks here on the config file.
Configuration Rollback
Whether you have altered the setup of your modem, you can always use Cisco software’s Configuration Rollback function to reinstate it to its former condition. You can accomplish this by running a command to see what changes were made to the configuration. Out which configuration modifications were needed, run the command to show the system commit involve. Before you know what changes were made, you could use the inverse configuration command to return the setup to its previous condition.
The transactional processing model, which is used in database systems, inspired the notion of rollback. A DBMS transaction may include a series of changes to a data store. You then must make a decision to either dedicate the adjustments (implement them indefinitely) or roll them back (discard the changes and return the table to its previous state). In this frame of reference, rollback means that a journal document containing a change log is tossed aside, and no adjustments are implemented. The rollback procedure restores the system to its previous state, prior to any modifications.
Before making any configuration changes, save the Cisco IOS running configuration if you want to use the configuration rollback feature. After making changes to the configuration, you can use the saved configuration file to reverse the changes (using the configure replace target-url command). Besides that, since you can use any saved Cisco IOS configuration file as the replacement configuration, you are not limited to a certain amount of rollbacks, as certain rollback designs are.
By changing the existing based adaptive with the stored structure, the Configuration Replace feature can restore the configuration to its previous state. The configuration that results will be the one that was on the system when you last saved it. You can use this function to undo any layout adjustments done since the configuration file was last saved. Admins can access this alternative only after logging into the Cisco software and enabling the correlating characteristics.
Exclusive Configuration Change Access feature
Exclusive Configuration Change Access (also known as the “Configuration Lock” feature) gives you exclusive access to the running Cisco IOS XE configuration, preventing multiple users from making concurrent configuration changes.
The Access Session Locking augmentation from the above characteristic extends the Exclusive Configuration Change Access feature so that show and debug commands entered by the user holding the configuration lock always have prioritized implementation; exhibition and debug orders decided to enter by other users are only permitted to run after the procedures begun by the configuration lock holder have finally completed.
The locking mechanism used throughout the Configuration Replace and Configuration Rollback functionalities work in tandem with the Exclusive Configuration Change Access feature (“exposed lock”) (“rollback lock”).
The Cisco software Exclusive Configuration Change Access feature allows one or more administrators to lock the configuration of their devices. When you make a configuration change, the device’s behavior changes. By locking the configuration mode every time a user enters or exits the device’s CLI or telnet SSH interface, the design prevents concurrent modifications. You can use this feature to protect your data by preventing unauthorized network configuration settings.
To enable the Exclusive Configuration Change Access feature in configuration mode, are using the implemented appropriately entirely separate command. Exclusive Configuration Change Access can indeed be established to auto, which also locks the Cisco IOS XE configuration mode every time the configure port command is approved, or manual, which locks the Cisco IOS XE configuration mode only when the configure terminal lock command is issued.
On the very same router, you can prevent multiple users from modifying the same configuration file. If two users attempt to make changes at the same time, they may clash. Actually, enable the Cisco software’s Exclusive Configuration Change Access feature to protect this. You can check which users are currently in the exclusive session after facilitating this feature. Use the “show configuration lock” command to display the current status of all exclusive sessions in order to shut down the configuration. You can choose which user to lock and which to allow the performance.
Unicast RPF

You are probably aware of Unicast RPF. This software limits malicious traffic on your grid by ensuring that packets are routed to match the advertised route. Unicast RPF can prevent spoofed IP addresses by verifying the reachability of source addresses’ inboxes. To implement Unicast RPF on your network, ensure you have a Cisco router.
If you want to know more about Unicast RPF, check out this Cisco software. You’ll soon see how useful it is in your network. It can also handle traffic based on ACLs and allows unicast packets to be dropped or permitted. This software is easy to install and configure, so it’s essential to have a Cisco router with Unicast RPF enabled.
Conclusion
The next step in narrowing down your options is to eliminate tools that aren’t suitable for the number and size of gadgets in your system. Our list contains tools ideal for small networks and devices appropriate for large systems. Some might be suitable for businesses of any size. You should also pay close attention to the vendors of your network equipment. If you have all of your network equipment from Cisco Systems, you can get any software devices on this list.